Authentication for Casewhere Admin
Introduction
The Casewhere Admin site acts as a SAML2 (Security Assertion Markup Language 2.0) service provider, meaning it relies on identity providers (IdPs) that support the SAML2 protocol for authenticating users. The flexibility of this setup allows Casewhere Admin to integrate with a variety of IdPs, as long as they are compatible with the SAML2 standard.
This guide will specifically cover configuring authentication for the Casewhere Admin site using Identify as the IdP. However, the steps outlined are broadly applicable and can also be used when integrating Casewhere Admin with other SAML2-compatible IdPs. Additionally, these instructions can be applied to configure authentication for the Casewhere Job site using Identify.
Prerequisites
- Casewhere Admin is up and running.
- Identify is up and running.
Configuration steps
Create SP signing certificate
An SP (Service Provider) signing certificate in SAML (Security Assertion Markup Language) is a digital certificate that the Service Provider uses to sign SAML authentication requests and, in some cases, SAML assertions before sending them to the Identity Provider (IdP). The IdP then uses the public key from the SP's signing certificate to validate the signature, ensuring the integrity and authenticity of the data.
Step 1: Create a signing certificate. You can follow the guideline here to generate a self-signed certificate, which is sufficient for most deployments.
Step 2: Install the certificate, including the private key, on the Casewhere web server, and ensure that IIS_USRS has permission to read it.
Step 3: Export the public key and upload it to the Identify server. Log in to Identify Admin, navigate to System Setup > Manage Certificates, and select Certificate > Import to upload the public key of your signing certificate. Identify will use this key to verify requests sent from Casewhere.
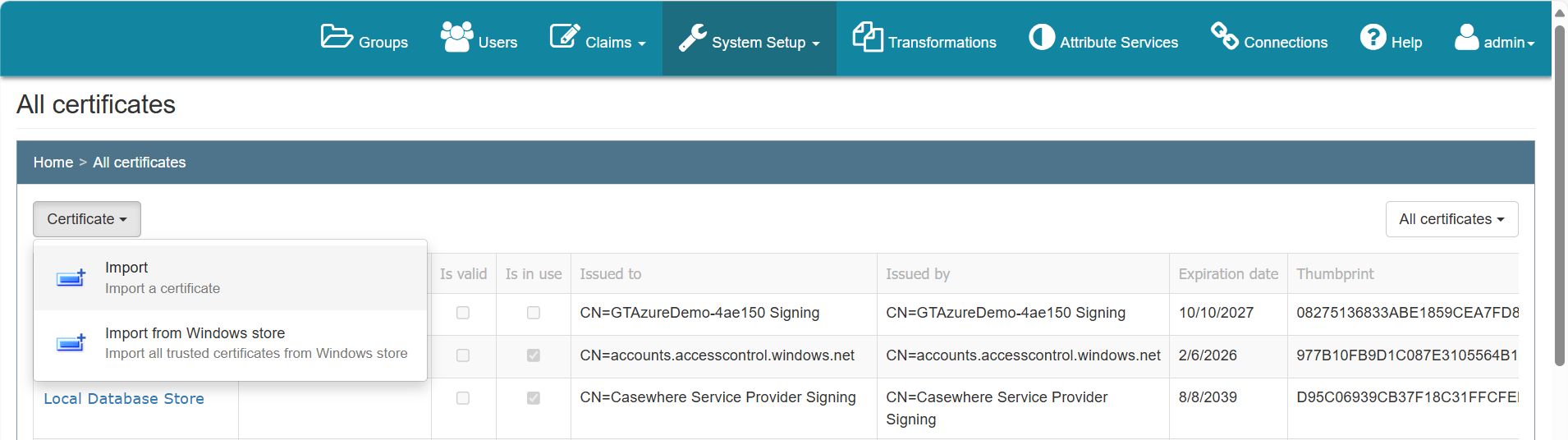
Configure Casewhere
Configure IdP settings in the web.config of Casewhere Admin
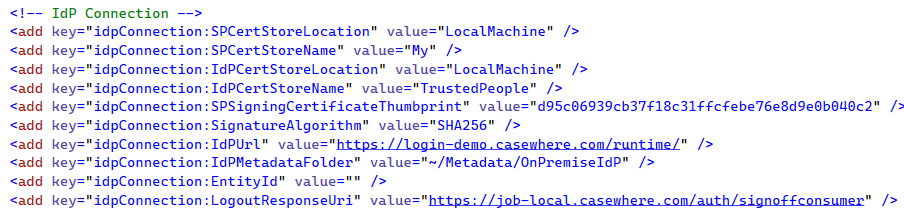
- idpConnection:IdPCertStoreLocation and idpConnection:IdPCertStoreName: The location where you install the Identify’s signing certificate. The certificate can be downloaded from Identify.
- idpConnection:SPCertStoreLocation and idpConnection:SPCertStoreName: The location where you install the Casewhere’s SP signing certificate.
- idpConnection:SPSigningCertificateThumbprint: The private key Casewhere uses to sign requests before sending to Identify.
- idpConnection:IdPUrl: URL of the Identify Runtime, e.g., https://login-local.casewhere.com/runtime/.
- idpConnection:IdPMetadataFolder: The virtual path to the folder containing the metadata.xml provided by the IdP.
- idpConnection:LogoutResponseUri: The URI Casewhere uses to handle the logout callback from IdP.
- idpConnection:EntityId: The identifier of the Casewhere app as part of the protocol. If not specified, Casewhere will use the application domain name as EntityId to communicate with IdP.
Configure Identify connection
Login to Identify Admin and navigate to Connections, select New, and a dropdown menu will appear:
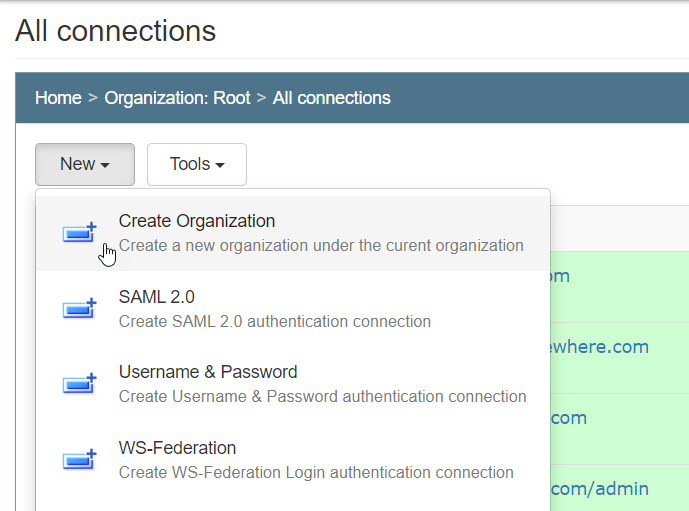
Create a new SAML 2.0 protocol connection with the following settings:
- Name: [service provider name] e.g. https://admin-local.casewhere.com
- Enabled: true
- Authentication connection: e.g., Username & password. You can learn how to set up an Identify authentication connection here.
Click Save and Close; a connection will be created.
In the connection list, navigate to the connection you just created and select Upload metadata.

The upload metadata dialog will appear. Here, you have two options:
- Enter the metadata URI [Casewhere Admin domain]/auth/metadata, e.g., https://admin-local.casewhere.com/auth/metadata.
- Upload the file from your machine.
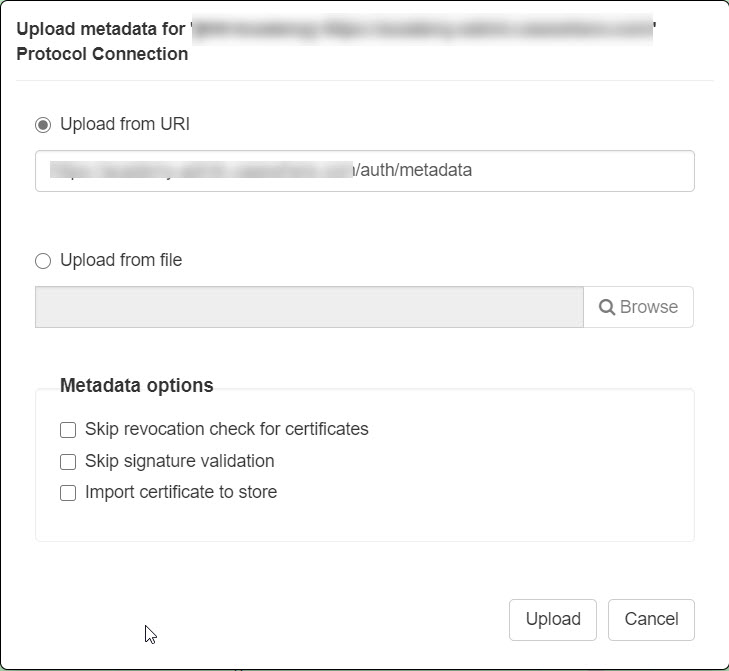
You can skip the revocation check for certificates and signature validation for deployments where self-signed certificates are utilized.
If the configuration is done correctly, when you visit the Casewhere Admin site, you will be directed to Identify where you can enter your login credentials.